Cyber Security Machine Learning Based Model
ADELean4CSA – Artificial Intelligence at Work An Anomaly Detection Engine for an Assisted Cyber Security Defence
ADELean4CSA
Is an “always-on” intelligent assistant based on a non-supervised Machine Learning engine who continuously learns, and without any pre-determined rules, is able to detect suspicious anomalies on the network.
It immediately alerts security operators to focus their attention and let them choose the best countermeasure.

ADELean is a software,
- Does not overlap to any Security Operation Centre technology, but only supports them
- Easy to install
- Works seamless in complex operational environments
- It is immediately ready to operate
- Identifies both internal or external threats
- It is designed with a Big Data scalable architecture
- It embeds a powerful high-performance Machine Learning engine able to process high volume of data in real-time
- Compliant to any privacy regulation, as no need to read the content of the traffic packages
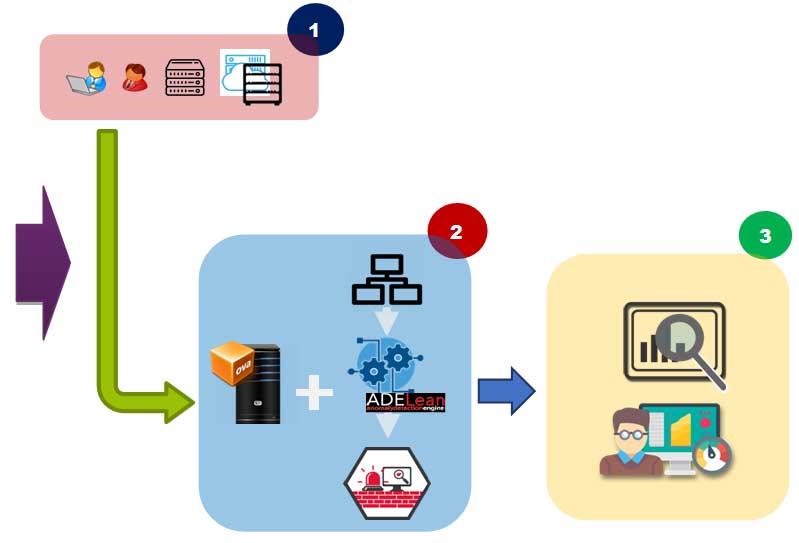
HOW IT WORKS:

COLLECT
Collect traffic data directly from the core switches and only stores headers. Des not need to read and interpret the content of the network packages.

ENRICH & ANALYZE
The collected data are analysed by the engine based on proprietary ML algorithms in 2 steps. Step 1 - extraction of all information through the construction of hundreds of anomaly indicators. Step 2 - train the algorithms to calculate the anomaly scores of each session.

SHOW
The identified anomalies are presented in a dashboard that provides an overall picture through a set of KPIs about network status and detailed reports to let operators accurately examine each anomaly and plan the necessary actions using their current process and procedures.

CUSTOMAZATION
OPTIONAL ADELean operates "out of the box" but it is customizable to specific needs through the construction of ad-hoc anomaly indicators. These custom KPIs may be designed with the help of customer's security experts. The rest of the analysis procedures does not require any customization.
Ease of Enhancements & Customizations
Totally Open
- Inside components integration
- data sources integration
- New machine learning model (i.e. network wide holistic model)
Setup activities
Phase I – Analysis:
- Scope definition
- Data sourcesanalysis
- Sizing
- Environment setup
Phase II – Installation:
- OVA/Physicalinstallation
- Netflowconfiguration
- SIEM integration (optional)
Phase III – Golive:
- ADELean up and running
- Installation documentationreleased
5 workingdaysoverall
Onsite/remote activities